IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 18 countries to choose from, rental period from 2 days.
Resident
From $0.70 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
In many networks, traffic is automatically redirected through an intermediate server – without any visible signs on the device or in applications. This approach is used in schools, offices, guest Wi-Fi – everywhere control over access and online activity is required. From the user’s perspective, everything looks like a regular direct connection, although, in reality, additional network mechanisms are involved. One such tool is a transparent proxy.
This solution allows requests to be intercepted and content to be filtered, with data being cached and user activity analyzed without any involvement from the client. This technology offers clear advantages for administrators, but it also comes with certain technical limitations. For additional insights into other types of proxies and their pros and cons, it can be useful to explore different shared proxies and their use cases.
A transparent proxy is a server that secretly processes traffic between the user's device and the internet at the infrastructure level. It receives data even before it reaches the target server and can perform various operations, including filtering, caching, and logging.
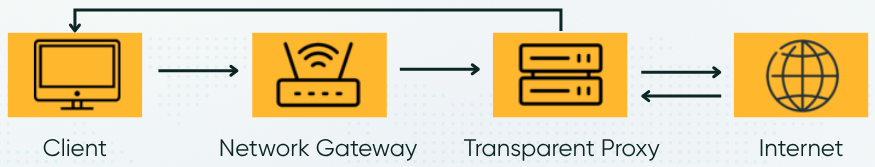
The necessary configuration is carried out at the network equipment level. This is handled by a system administrator or an information security engineer. The following tools and mechanisms are commonly used:
The operation of such a server depends on the type of requests being transmitted:
This approach does not require any client involvement, but provides the administrator with complete control over all inbound and outbound traffic.
This solution enables systems to follow established rules, regardless of user settings. It is effective in large or distributed networks (for example, in companies with remote branches and a unified network policy).
Key tasks addressed by this approach include:
Such intermediaries are used in various types of networks:
For businesses, transparent proxies are a means to centrally implement network security policies. IT specialists use these tools to control internet access, manage, filter, and analyze traffic at the infrastructure level.
Despite their widespread use, these types of proxy servers are not universal. They have technical limitations that can impact service operation, introduce security risks, and create compatibility issues with modern protocols. Below are the key vulnerabilities and constraints network specialists encounter when deploying this technology.
This solution does not hide the client’s IP address – in fact, it may add extra HTTP headers to requests, allowing the target server to identify the source:
As a result, the client becomes fully trackable, and using this solution precludes anonymity.
A transparent proxy cannot analyze HTTPS content without intervening in the SSL chain (for example, via certificate replacement). It can detect the fact of a connection but cannot decrypt the data. This leads to a number of problems:
Consequently, such solutions become impractical for working with web services that require strict security policies. Without full decryption of traffic, filtering and analytics are limited, which often results in failures for business-critical applications.
With insufficient protection or misconfigured proxy settings, such a server can become a vulnerability within the infrastructure.
Potential risks include:
Furthermore, if there are no restrictions on IP addresses and ports, the proxy server may be accessible externally, which increases the risk of exploitation by attackers—for example, for bypassing filters, traffic masking, or carrying out DDoS attacks.
In practice, this may also cause issues with VPNs, mobile apps, anti-fraud systems, and services that rely on geolocation or stable IP addresses. Under such circumstances, this solution shifts from being a management tool to a potential point of failure—requiring either circumvention or a change to the overall network architecture.
The key difference between these types lies in how they interact with client devices, their configuration methods, and intended use cases.
A transparent proxy intercepts data from the client without their knowledge or involvement. The user connects directly to a website, but their traffic is automatically redirected to a host (for example, at the level of a router or firewall).
An explicit one requires the client to be aware of its presence in advance. The device (browser, OS) sends requests not to the target site, but to the proxy server’s address, which then forwards the requests further.
An explicit proxy requires configuration on every client – manually or using specialized tools (PAC file, GPO, MDM). This increases the level of control, but also demands additional effort from IT specialists for setup and device support.
A transparent proxy is configured exclusively at the network infrastructure level (router, gateway, firewall).
Transparent servers are most often used for invisible monitoring and filtering of transmitted data, monitoring, caching, and ensuring security in organizations, schools, public Wi-Fi, etc.
Explicit proxies are used where routing flexibility, fine-tuned policy management, and anonymization are required. For example, in corporate environments with strict security and access control requirements, or where logging is essential. They are also utilized when high levels of security and privacy are necessary, especially when using high-cost solutions such as elite proxies, which allow for precise control over every connection at the proxy level.
| Criterion | Transparent | Explicit |
|---|---|---|
| Visibility to Client | Invisible, requires no configuration | Configured manually or centrally |
| Configuration | At the router, gateway, or firewall level | On the client device |
| System Behavior | Does not log proxy participation in data transfer | Sends requests directly to the proxy server, not the target resource |
| Management Flexibility | Limited by infrastructure settings | High: granular filtering, routing, exclusions |
| Usage | Monitoring, filtering, caching of network requests | Managed access, user identification, anonymity, reporting |
Despite the absence of explicit settings on the client side, the presence of a transparent one can be identified by certain technical signals and anomalies in network behavior.
Typical signs:
HTTPS connection characteristics:
Tools for checking:
Using several of these methods together helps more accurately determine whether a transparent proxy server is present in the network.
Transparent proxies are a useful tool for centralized traffic control, filtering, and enforcing network policies without user intervention. However, they can cause difficulties if priorities include confidentiality, stable operation of encrypted connections, or individual traffic routing. Such conflicts are particularly noticeable in hybrid and latency-sensitive networks.
Understanding the principles of how this solution works, its limitations, and possible workarounds helps to choose tools more accurately based on specific tasks, risks, and technical requirements.
Some analytics systems may record the IP address of the proxy server rather than the end client. This can distort geolocation data, behavioral metrics, and the operation of antifraud systems.
Yes. Many services require a secure channel and precise IP binding. Interference with traffic, especially the addition of headers or disruption of TLS sessions, can cause errors.
Yes. In some cases, administrators combine different types of intermediaries. The first is used for basic filtering, and the second for more precise routing or authorization.
