IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 18 countries to choose from, rental period from 2 days.
Resident
From $0.70 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
Web Real-Time Communication (WebRTC) is a browser standard that enables direct peer-to-peer audio, video, and data streaming – without the need for plugins or add-ons. It powers web conferencing, file sharing, and live streaming tools by handling all media and networking internally. However, because WebRTC relies on JavaScript APIs such as RTCPeerConnection and STUN, it can bypass VPN or proxy settings and expose your original address to websites and peers. To disable WebRTC is an effective measure to prevent IP leaks and maintain anonymity while browsing. Note that turning off WebRTC may restrict access to certain web features, including video calls and real-time applications. For most users, it is recommended to disable it only when strong privacy is required.
For gaming enthusiasts and developers who use platforms like Steam, WebRTC leaks can compromise IP security. Using a reliable proxy for Steam helps maintain privacy and stable access. You can read a detailed guide here on how to implement such protection.
Follow the steps below to turn off web real-time communication in this browser:
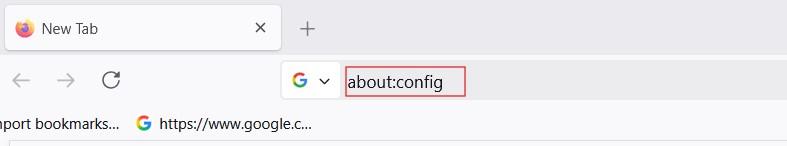
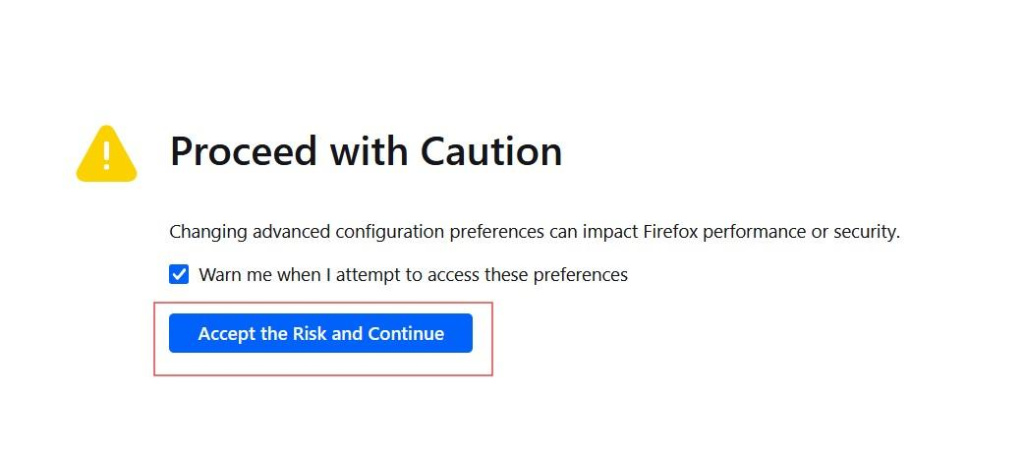
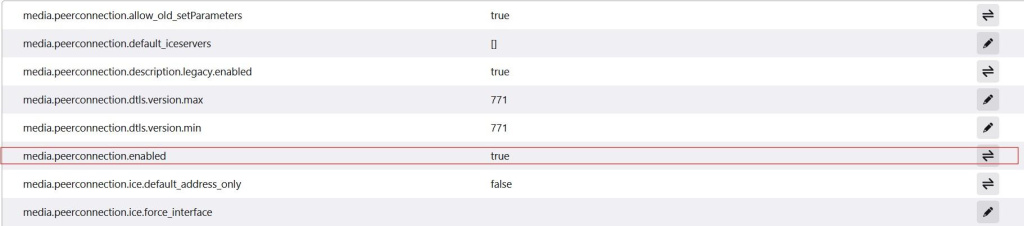
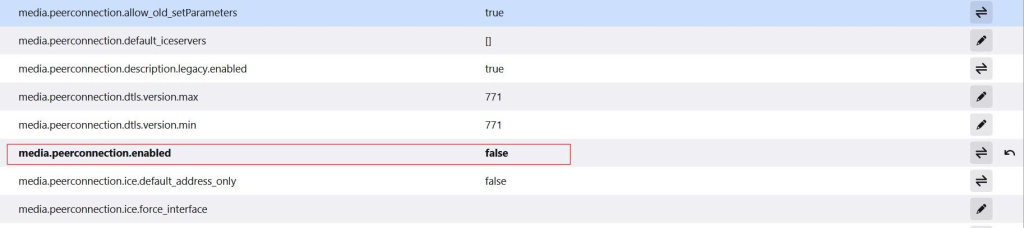
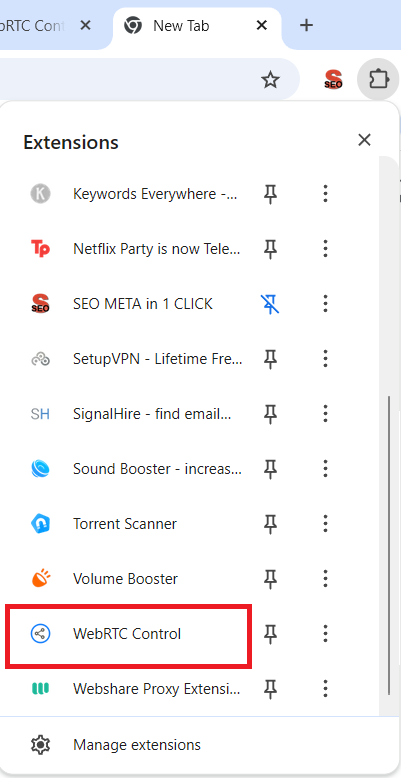
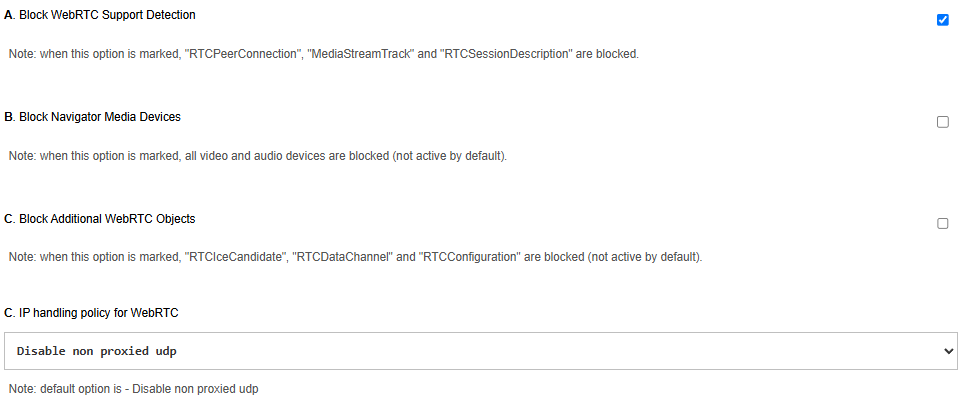
If the task is to disable WebRTC in Chrome, it’s possible to do only with specific extension called WebRTC Control:
The same method is applicable for the Opera.
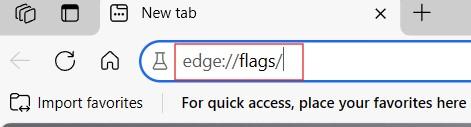
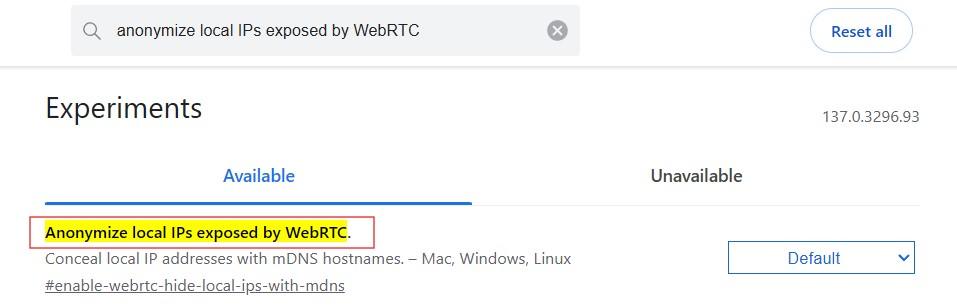
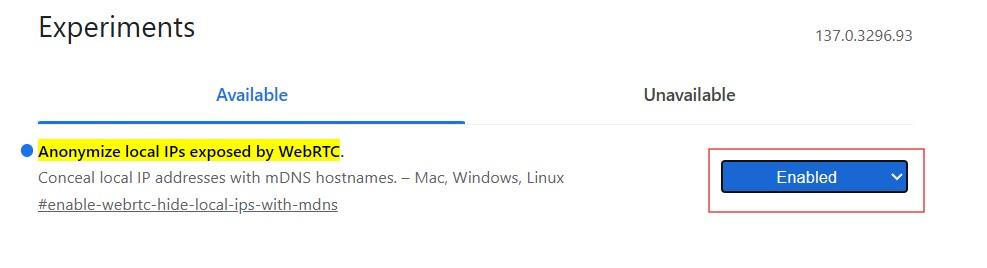
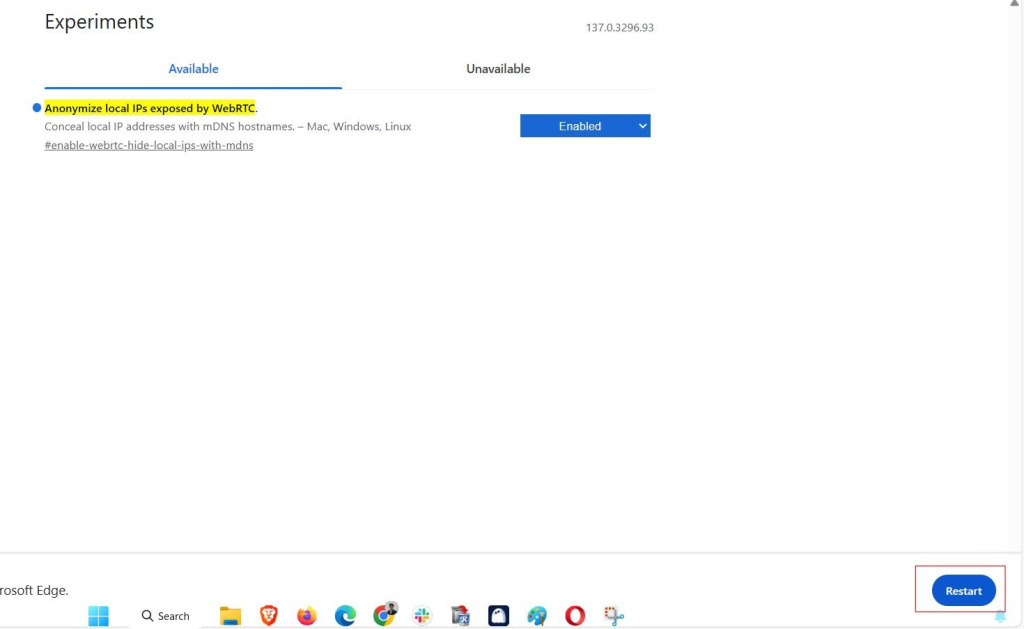
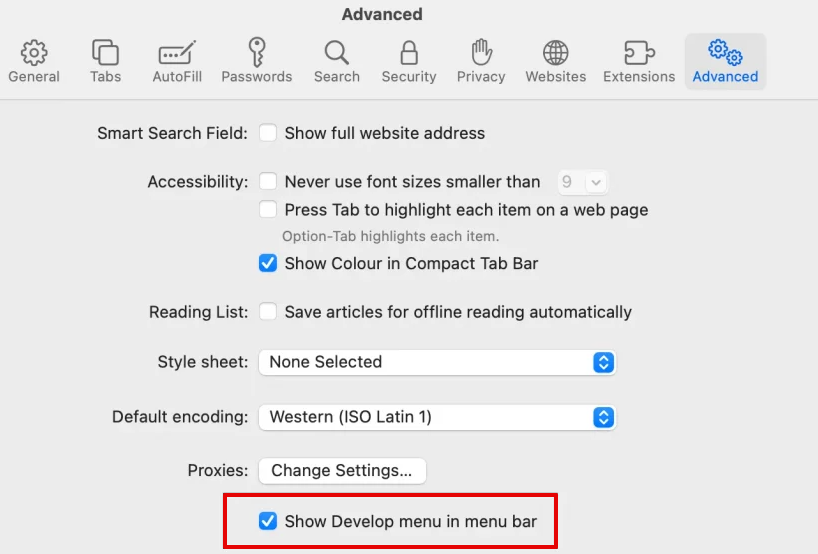
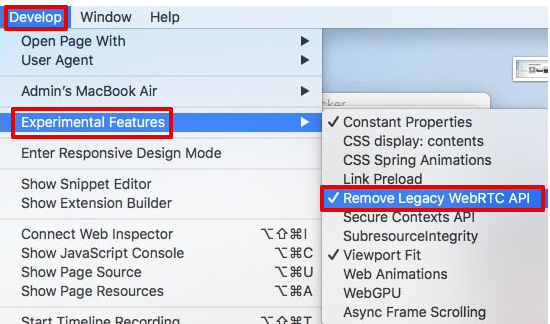
To sum up, disabling WebRTC prevents leaks caused by browser APIs. Desktop users can easily do this with extensions. Edge users can enable the flag to block local IP transmission. Safari users can configure their Desktop menu settings to get WebRTC disabled.
Regardless of the browser, validating the changes via reputable leak test tools is essential to ensure that WebRTC-based IP exposure has been fully mitigated. Validate with a leak test site to make sure that no local, public, or fake IP is seen. This should be part of any privacy routine alongside VPNs, proxies, and secure configurations.
