IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 18 countries to choose from, rental period from 2 days.
Resident
From $0.70 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
For proper routing and IP address management, a clear division and organization of network traffic is required. One of the basic tools in this process is the Subnet Identifier or Subnet ID – an element of an IP address that determines which network segment a device belongs to. This article explores how it works, the different types of subnets, how IPv4 and IPv6 architectures differ, and the role the subnet identifier plays in networks and proxy infrastructure.
It is a bit sequence allocated within an IP address to logically designate a specific network segment inside a larger address space. In IPv4 networks it is formed using the subnet mask, which separates the network portion of the address from the host portion. Here it becomes essential to understand what part of the subnet mask represents the subnet id, since this determines the device’s membership in a specific subnet. In IPv6, a similar task is handled using a prefix length that defines the number of bits assigned to the network identifier.
The use of a Subnet ID allows routers to efficiently direct packets between nodes within the same subnet and accurately determine the boundaries of network domains. This reduces channel load, lowers the number of broadcast requests, and simplifies the implementation of security policies.
Subnet classification can be based on the type of address space and intended use cases.
There are also classes of IP addresses that indicate network size:
In modern networking, CIDR addressing is used – classless inter-domain routing, which allows for creating subnets of arbitrary size rather than being limited to fixed classes.
The fundamental differences between IPv4 and IPv6 subnets lie in the structure of the IP space and scalability. IPv4 uses 32-bit identifiers and supports a limited number of unique Subnet IDs. Masks allow the creation of ranges from /8 to /32, providing flexibility but limiting the number of hosts.
IPv6, on the other hand, operates with a 128-bit scheme of allocation, which ensures an almost unlimited number of unique identifiers. For most subnets, a /64 mask is used, with the remaining 64 bits reserved for device identification.
Let’s examine the key differences:
| Parameter | IPv4 | IPv6 |
|---|---|---|
| Address Length | 32 bits | 128 bits |
| Scalability | Limited (around 4.3 billion addresses) | Practically unlimited |
| Format | 192.168.1.1 — decimal, 4 octets separated by dots | 2001:0db8:85a3::8a2e:0370:7334 — hexadecimal, 8 blocks separated by colons |
| Mask | /8 – /32 | Typically /64 |
| Security | Limited, requires additional configuration | Built-in encryption and ACL mechanisms |
IPv6 also provides integrated security and auto-configuration mechanisms, which simplifies support for large distributed networks. However, since this is a newer format, it is important to check whether a particular website supports IPv6. Compatibility testing with web resources is quick and easy using online checkers.
In some cases, proxy providers may issue users IPv6 addresses that contain an IPv4 component — essentially IPv6-compatible addresses presented in hybrid form for easier configuration.
The Subnet ID helps optimize key aspects of infrastructure management. By dividing traffic into subnets, routing is handled locally, which reduces latency, prevents channel overload, and improves performance. Subnets isolate individual segments, ensuring that threats or failures in one area do not spread to others.
From a security standpoint, subnet division simplifies the implementation of security policies, access restrictions, and firewall configuration. The administration of IP spaces becomes more structured, which is particularly important for scalable solutions. An additional identifier also contributes to efficient address allocation and helps avoid conflicts, especially in IPv4 address spaces. This principle is based on the separation of the subnet mask network ID and host ID, where the network ID defines the subnet boundaries and the host ID specifies individual devices within that subnet.
If you want to know how to get a Subnet ID from an IP address, it is performed by a system administrator using the base address and mask. The IP range acts as an identifier for the overall system, while the mask defines which part of the value refers to the entire block and which part specifies the host within it. This method allows the creation of separate logical subnets within the same physical infrastructure, enabling independent management.
Creating subnets involves step-by-step allocation of smaller ranges from the existing IP pool. First, the required number of divisions is determined, then the number of additional bits needed for subdivision is calculated. A new mask is formed by increasing the prefix length of the original block.
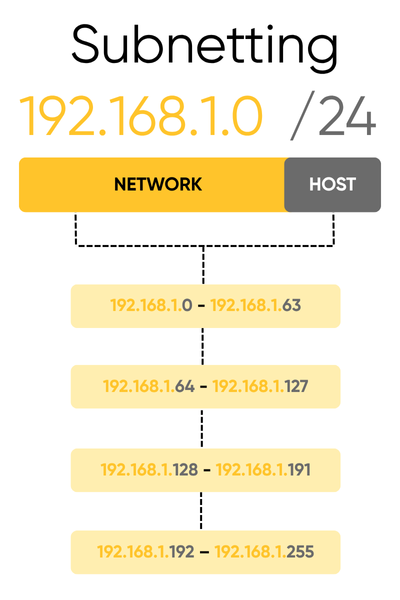
For example, if the address space 192.168.1.0/24 needs to be divided into 4 subnets, 2 additional bits must be reserved (2² = 4), resulting in a new mask /26.
Final ranges will be:
Each of these subnets has its own identifier and can be independently configured.
Such segmentation allows assigning individual security and routing policies, restricting interdepartmental access, and simplifying infrastructure interaction audits.
Each of these provides the required address pool and enables centralized management of access to both local and external resources.
In proxy infrastructure, the Subnet ID is used for load balancing, enhancing anonymity, and optimizing routing. Dividing IP addresses into subnets makes it possible to implement a distributed scheme for internet access, which reduces the risk of blocks and ensures more stable connections in high-load scenarios. Additionally, it helps isolate traffic from different users or services, providing secure routing of requests.
For more on intermediary servers, see the article “Backconnect Proxies”.
The Subnet ID is a key element in building modern network architecture. Its use contributes to routing optimization, traffic isolation, improved security, and efficient IP address allocation. With the continuous growth of infrastructure demands, it remains an effective tool for segmentation and managing resources, especially when combined with proxy technologies and flexible addressing schemes.
