IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv4
From $0.72 for 1 pc. 37 countries to choose from, rental period from 7 days.
IPv6
From $0.07 for 1 pc. 14 countries to choose from, rental period from 7 days.
ISP
From $1.35 for 1 pc. 23 countries to choose from, rental period from 7 days.
Mobile
From $14 for 1 pc. 18 countries to choose from, rental period from 2 days.
Resident
From $0.70 for 1 GB. 200+ countries to choose from, rental period from 30 days.
Use cases:
Use cases:
Tools:
Company:
About Us:
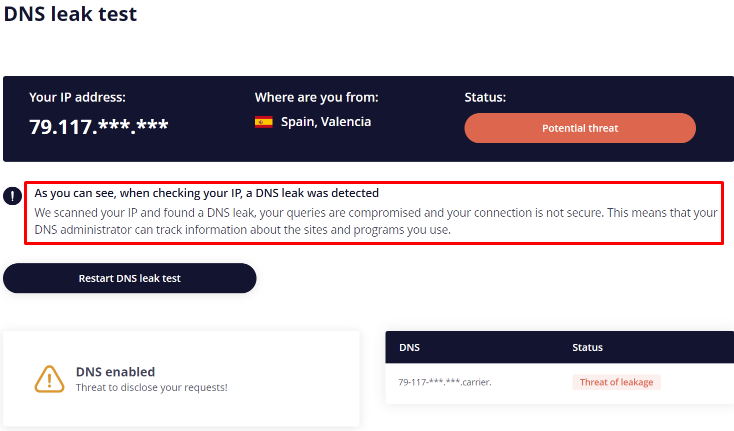
A DNS leak occurs when DNS requests are sent outside of a secure, encrypted tunnel – such as through your ISP's servers – even if you're connected to a proxy or VPN. This allows third parties to view your browsing history despite masking your IP.
Knowing how to stop DNS leaks is essential for users who rely on proxies and anti-detect browsers to maintain privacy and bypass regional restrictions. Whether you are managing multiple accounts, accessing content unavailable in your location, automating your workflow, or simply concerned about anonymity, a leak undermines the purpose of any privacy tool.
Therefore, in this guide, you will learn what the Domain Name System vulnerability is, its common causes, and how to address such issues to ensure the security of your data and implement reliable protection.
When you visit a website, your device sends a request to the DNS server, which returns the correct IP address so the browser can load the site. However, if you are connected to an active proxy, the request should be channeled through its servers to conceal your digital footprint. So, a leak indicates that the request was routed outside the secure server, such that your internet service providers and third parties can map out your browsing activities. Also, a leak exposes any attempt to avoid tracking, your actual location, and all websites you visit.
This kind of vulnerability is a major concern as it creates serious security risks, especially for users who depend on privacy tools. Compromised DNS data can be logged, used for profiling, or even sold, undermining online security and confidentiality.
Several factors, like operating system errors and network issues, can compromise anonymity. As a result, your ISP, as well as other third parties, including cyber attackers, can monitor your online activities. Below are some of the main causes of leaks and how they undermine your privacy:
Leaks often occur when the proxy or VPN server is misconfigured and fails to redirect DNS queries through secure servers. Therefore, if your network traffic defaults back to your ISP’s DNS configuration even after configuring an intermediary server, every request from your network is visible to your ISP, which puts you at a disadvantage. A simple way to avoid this issue is to use proxies with built-in leak protection and ensure they send your network traffic through their secure channels.
Windows 10 and newer versions come with a built-in feature called Smart Multi-Homed Network Resolution. It aims to resolve DNS queries with all available network adapters (Ethernet and Wi-Fi) at the same time. Although this feature was designed for faster responses, it can cause leaks in the queries even when connected to a secure intermediary. To fix this problem, opt for an intermediary service that overrides the feature on Windows or disable said feature via Registry Editor.
Switching networks, like going from Wi-Fi to mobile hotspots, can temporarily disable privacy settings. As a result, the operating system may revert to its default settings and send requests via the ISP DNS server. Always remember to disable intermediaries before switching networks and enable them once the swap is complete.
Some Internet Service Providers use transparent DNS proxies to intercept your traffic, exposing you to censorship and content blocking. As a result, even if you change the Domain Name System settings of your network, they are forcibly redirected towards the ISP servers. To prevent interception of the traffic, deploy encrypted protocols like (DoT) or (DoH).
The Windows operating system has another built-in feature called Teredo that may interfere with encrypted DNS protocols. Microsoft designed Teredo to ease the transition between IPv4 and IPv6 so they can coexist without problems. However, this creates a vulnerability for proxy users as Teredo is a tunneling protocol that may supersede configured intermediary servers and cause leaks. To regain security and anonymity, you can disable Teredo by opening a Command Prompt window and entering “netsh interface teredo set state disabled.”
Some leaks occur due to IPv6 traffic and Web Real-Time Communication (WebRTC), which can bypass proxies and reveal its queries. If you don’t need IPv6 on your PC, you can disable it to avoid security breaches. Additionally, use extensions to block WebRTC or choose proxies that have the ability to block WebRTC leaks. If you want to understand how WebRTC exposes real IP addresses and how to properly disable it in browsers to avoid data leakage, you can read our detailed guide on how to disable WebRTC.
Malware on your operating system can modify its settings, which makes you vulnerable to spoofing. As a result, your queries may be redirected to rogue servers for monitoring, phishing, or even data extraction.
Several tools are available to help you determine the possibility of leaks. In this section, we will explore how to check for DNS leaks using online tools and manual methods.
There are extensions and apps that allow you to track all inbound and outbound network traffic from your computer. As a result, you can see the servers that send requests originating from your device.
WebRTC vulnerability checks help confirm whether the technology is revealing your network details, even when connected to an intermediary server. Online WebRTC detection tools can be used to assess the threat.
You can leverage online testing platforms to verify potential DNS disclosures. These services analyze the DNS servers that receive requests from your device. For example, BrowserLeaks.com and DNSLeakTest.com provide insights into whether your traffic is routed through a secure server or handled by your ISP.
Using such tools is the fastest and most convenient method to identify DNS vulnerabilities. Here is how to run a check with our website:
Fixing a leak is not only about bridging security but about learning how to prevent DNS leaks. Below are some practical methods to protect against it:
Using a proxy alone does not guarantee DNS encryption. For traffic to be secured, you need to configure the system or app to tunnel it through the proxy or use encrypted protocols like DoH or DoT. You can configure a proxy via the system’s settings, install an extension, or use Proxifier for detailed settings. Additionally, you can use such solutions as anti-detect web browsers with premium proxies to prevent a breach in network security.
Another practical DNS leak fix is to use a Firewall. They can be configured to prevent data from leaving your network including information in DNS requests. A firewall can block outbound requests to unwanted servers, ensuring that its traffic only passes through trusted or encrypted channels.
Manual configuration optimizes privacy as it prevents the use of ISP servers for its requests. Here is how to get it done on Windows operating system:
![]()
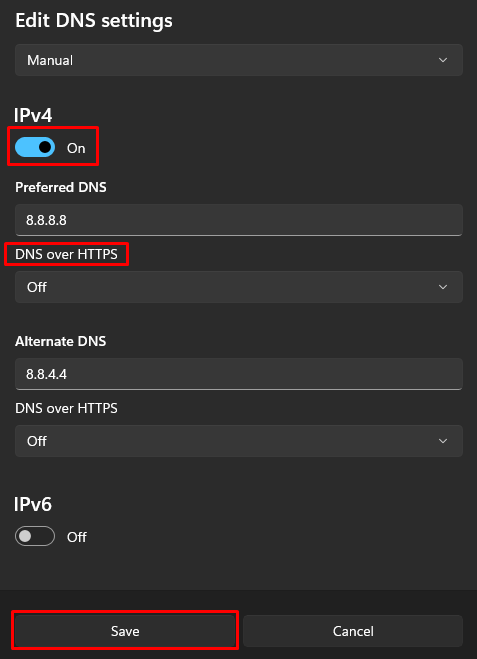
N.B: Google, Cloudflare, and OpenDNS are some of the most popular privacy-focused public providers that can be used for manual configuration.
Your computer often caches its information, which may remain on the system even after changing the settings. Therefore, clearing its cache is an effective method to ensure that only the new settings are used by the operating system. Below are some codes to clear any of its outdated information on your system: do this based on your system.
For Windows:
ipconfig /flushdns
For macOS:
sudo dscacheutil -flushcache; sudo killall -HUP mDNSResponder
For Linux:
sudo systemd-resolve --flush-caches
Some leaks originate from the router level. Misconfigured settings on the router or outdated firmware may cause your devices to revert to their default ISP servers. Therefore, a firmware upgrade may fix the leak. Additionally, you can configure the router settings to use the servers from secure providers so that all devices on your network will be protected from any potential leak.
Another practical tip to fix DNS leaks is to use encrypted protocols to prevent spoofing. DoT – DNS over TLS encrypts it through a TLS connection, which is different from the usual HTTPS traffic. On the other hand, DoH – DNS over HTTPS sends requests over HTTPS to prevent tracking.
Regular tests are recommended to ensure your configuration remains secure. Use online DNS test platforms like dnsleaktest.com to check your network status. Make sure to perform these checks whenever you switch networks, update software, or change IPs to detect any weaknesses and promptly address them.
DNS leaks are one of the most common yet overlooked threats to online security and privacy. Even when connected to an intermediary server, DNS requests can still be exposed to ISP servers, revealing your location and browsing patterns to third parties. To strengthen protection, it's also useful to understand how different security tools work - for example, you can explore the difference between a proxy vs a firewall in this detailed guide. Using high-quality proxies, disabling features like IPv6 and WebRTC, and running periodic tests are effective measures to minimize such vulnerabilities.
Learning how to prevent DNS disclosure goes beyond anonymity—it’s about gaining full control over your digital footprint. Follow the steps in this guide to keep your activities private, and don’t forget to use premium proxies for stronger protection.
DNS hijacking, also known as redirection, occurs when malicious parties take control of the server. Once this happens, they can redirect users’ requests to fake versions of websites to steal their data. In other cases, malware (designed for hijacking) on the system can override a device’s TCP/IP configuration to redirect traffic to malicious websites.
Testing for leaks should be done regularly, especially:
The test usually involves sending a series of requests from your device. It then monitors which servers respond to those requests and determines if the anonymity tool (like a proxy server) is actually hiding your original IP address and location.
